Email Authentication
Email remains a critical communication tool for businesses, making the security and authenticity of email messages more important than ever. Implementing effective email authentication strategies not only protects your brand but also ensures your emails reach your customers’ inboxes safely. Essential strategies for improving email authentication, providing a blueprint for businesses to enhance their email security and deliverability.
5 Essential Strategies for Improving Email Authentication
- SPF (Stand for Sender Policy Framework). It helps to verify that messages sent from specific IPs and servers. Messages are authorized by the domain owner. SPF reduce the likelihood of email spoofing.
- DKIM stand for DomainKeys Identified Mail. DKIM adds a digital signature to email messages, ensuring the sender’s identity is verified and the content is unaltered during transit.
- DMARC (Domain-based Message Authentication, Reporting & Conformance) enforces SPF and DKIM authentication, giving domain owners control over how their email is handled and providing reports on delivery status.
- BIMI (Brand Indicators for Message Identification) allows businesses to display their brand logos in customers’ inboxes, enhancing recognition and trust.
- ARC (Authenticated Received Chain) improves the security of email forwarding by maintaining authentication results across subsequent email hops.
1. SPF | Email Authentication
Sender Policy Framework (SPF) is a critical component in the email authentication process, designed to prevent email spoofing by verifying sender IP addresses. SPF records are published in the Domain Name System (DNS) and list the mail servers authorized to send emails on behalf of a domain. This mechanism enhances email deliverability and helps maintain the integrity of the sender’s domain.
An SPF record typically looks like this:
V=spf1 include:_spf.example.com ~all
To implement SPF for your domain, follow these steps:
- Identify all the mail servers and IP addresses that send emails on behalf of your domain.
- Create an SPF record with the identified IP addresses and include mechanisms.
- Publish the SPF record in your domain’s DNS.
- Regularly update the SPF record to reflect any changes in your email infrastructure.
By diligently managing SPF records, organizations can significantly reduce the likelihood of their emails being flagged as spam or rejected by recipient servers.
It’s important to note that while SPF is a powerful tool for email authentication, it should be used in conjunction with other methods like DKIM and DMARC for a comprehensive email security strategy.
2. DKIM | Email Authentication
DomainKeys Identified Mail (DKIM) is a vital email authentication technique that enhances the security and integrity of email communications. DKIM adds a digital signature to your outgoing emails, which is a cryptographic hash of the message and your domain name. This signature is crucial for the recipient’s server to verify that the email has not been tampered with during transit.
To implement DKIM, follow these steps:
- Generate a unique private key for your domain.
- Publish the corresponding public key in your DNS records.
- Configure your email server to attach the DKIM signature to all outgoing emails.
The process of DKIM verification involves the recipient’s server using the public key to decrypt the signature and compare it with the hash of the message. If the key signature and hash message are matched, then the email is considered authentic.
By ensuring that the message body and attachments remain unaltered, DKIM plays a crucial role in maintaining the integrity of your domain and protecting against email spoofing.
Here is an example of how DKIM signatures appear in email headers:
| Header Element | Value |
|---|---|
| v | 1 |
| a | rsa-sha256 |
| d | example.com |
| s | 20180101 |
| c | relaxed/simple |
| q | dns/txt |
| i | @example.com |
| t | 1523606201 |
Implementing DKIM not only improves email deliverability but also builds trust with recipients, distinguishing legitimate messages from forged ones.
3. DMARC | Email Authentication
DMARC, which stands for Domain-based Message Authentication, Reporting, and Conformance, is a protocol that enhances email security by leveraging SPF and DKIM protocols. It provides a framework for email receivers on how to handle emails that fail authentication checks, aiming to reduce phishing and spoofing attacks.
When setting up DMARC, you define a policy that instructs email servers on the actions to take when an email does not pass SPF or DKIM checks. The options include:
- Rejecting the email outright
- Quarantining the email (placing it in a spam folder)
- Accepting the email but marking it for further review
Additionally, DMARC allows domain owners to receive aggregate and forensic feedback reports. These reports are crucial for monitoring authentication failures and understanding how your email domain is being used, which can inform further security measures.
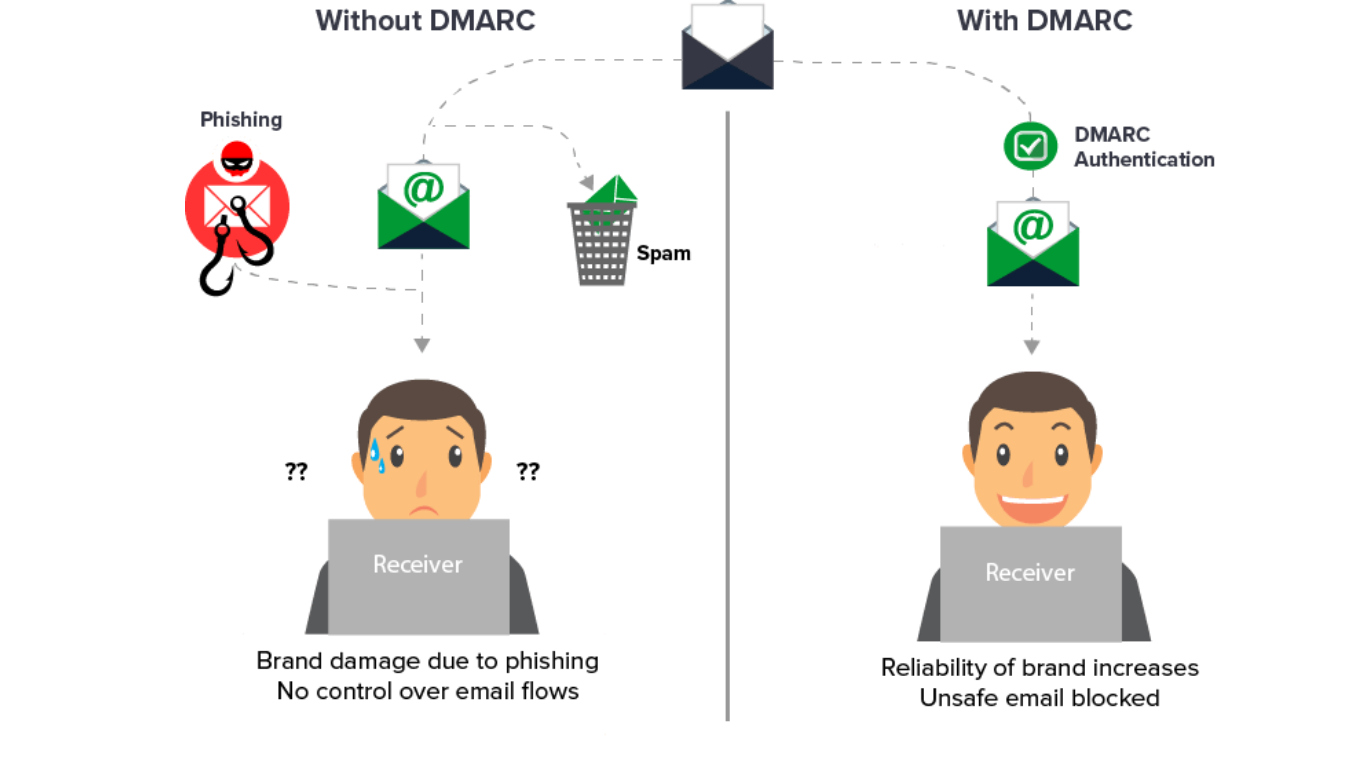
By implementing DMARC, organizations gain visibility and control over the email messages sent from their domain, ensuring that only authenticated emails reach their intended recipients.
Here is an example of a DMARC policy entry:
v=DMARC1; p=reject; rua=mailto:[email protected];
This entry specifies that emails failing authentication should be rejected and reports should be sent to the specified email address. The adoption of DMARC can significantly improve your email deliverability and security posture.
4. BIMI
Brand Indicators for Message Identification (BIMI) is a cutting-edge standard in email authentication that enhances the visibility and trustworthiness of your brand in the inbox. When implemented correctly, BIMI allows your brand’s logo to appear next to your email in supported email clients, such as Gmail, giving recipients a quick visual confirmation of the message’s authenticity.
BIMI is not a standalone solution; it works in conjunction with SPF, DKIM, and DMARC to ensure a comprehensive authentication framework. Here’s a simple breakdown of the requirements for BIMI implementation:
- DMARC policy set to enforcement
- Verified brand logo in SVG format
- Published BIMI record
BIMI serves as a trust signal in the inbox, reinforcing the legitimacy of your emails and potentially boosting deliverability.
Steps:
- Ensure that you have a DMARC policy in place and at enforcement.
- Obtain a verified SVG version of your brand logo.
- Publish a BIMI record in your DNS.
Remember, while BIMI adds a layer of trust, it’s crucial to maintain a good sending reputation and adhere to email best practices to maximize its benefits.
5. ARC
The Authenticated Received Chain (ARC) is a critical protocol that enhances the security of email authentication, particularly for forwarded messages. Unlike traditional methods, ARC allows mail servers to track the authentication status of an email through each entity that has handled it. This is especially beneficial for emails that pass through multiple intermediaries, such as those on mailing lists.
To effectively implement ARC, consider the following steps:
- Ensure that SPF and DKIM are already in place.
- Configure your mail server to attach ARC headers to outgoing emails.
- Verify that incoming emails contain valid ARC headers and authentication results.
ARC’s ability to maintain the integrity of email authentication across multiple forwards is what sets it apart from other protocols.
For organizations using Microsoft Defender for Office 365. It is important to configure trusted ARC sealers. ARC done through the Microsoft Defender portal by selecting the ARC tab and adding trusted entities.
Here is a structured overview of ARC’s benefits:
| Benefit | Description |
|---|---|
| Security | Enhances the trustworthiness of forwarded emails. |
| Compatibility | Works alongside SPF and DKIM. |
| Flexibility | Useful for emails that traverse multiple intermediaries. |
Conclusion
In conclusion, the importance of email authentication in today’s digital landscape cannot be overstated. As we’ve explored in this article, implementing key protocols such as SPF, DKIM, DMARC, BIMI, and ARC is essential for safeguarding your email communications against fraud and enhancing your brand’s credibility.
Regularly updating your authentication records ensures ongoing protection and trust with your customers. While the process may seem complex, the benefits of improved deliverability and a secure online reputation are invaluable for any organization. Remember, email authentication is not just a technical necessity; it’s a strategic investment in your brand’s integrity and customer relationships.
Frequently Asked Questions
What is SPF and why is it important for email authentication?
SPF (Sender Policy Framework) is an email authentication method that verifies if incoming mail from a domain comes from an IP address authorized by that domain’s administrators. It’s important because it helps prevent email spoofing and ensures that receivers can trust the source of the emails they receive.
How does DKIM improve email security?
DKIM (DomainKeys Identified Mail) adds a digital signature to email headers, which is verified against a public cryptographic key published in the sender’s DNS records. This ensures that the content of the email remains unchanged from the time it was sent, thus improving email security by preventing tampering.
What role does DMARC play in email authentication?
DMARC (Domain-based Message Authentication, Reporting, and Conformance) builds on SPF and DKIM protocols by allowing domain owners to specify how email receivers should handle messages that fail authentication checks. It also provides reports on email delivery status, making it a critical tool for managing and improving email authentication.
Can BIMI affect my email deliverability?
BIMI (Brand Indicators for Message Identification) allows brands to display their logos in supported email clients, which can enhance trust and brand recognition. While BIMI itself doesn’t directly affect deliverability, it can indirectly improve it by encouraging recipients to engage more with authenticated emails.
What is ARC and how does it help with email forwarding?
ARC (Authenticated Received Chain) is a protocol that helps preserve email authentication. It results across multiple ‘hops’ when messages are forwarded. This is particularly useful when emails pass through intermediaries that may alter the message, potentially breaking SPF or DKIM authentication. ARC ensures that the original authentication results are still available to the final recipient.
Are there best practices for maintaining email authentication effectiveness?
Yes, it’s essential to keep your email authentication records, such as SPF, DKIM, and DMARC, up to date as your email infrastructure evolves. By regularly reviewing and updating these records ensures that your authentication methods remain effective. Your emails due to mail authentication continue to reach their intended recipients without going to spam folder.


